Hacking - good or bad
Hacking - a word that foreign to you. Every in social media, you can also see some posts, videos or ads like "How to hack Facebook...

Hacking - a word that isn't foreign to you. Every in social media, you can also see some posts, videos or ads like "How to hack Facebook account", "Hack Facebook account in 5 minutes", "How to Hack subcribes in Youtube",.... So, do you know the nature of hacking?
What is hacking?
Hacking is trick that you go into a system that not of you, then replace something in this system that you hack. Hacking is also know like cheating. This activity like "you violate the privacy of someone that the author of the system don't accept".
A people has did the hacking is a hacker.
So, Hacking is bad or good?
As I talk at part "What is hacking?" , hacking is bad because it like cheating. But if you use hacking for good, it isn't bad.
How many types of attacking of hacking?
There are many types of hacking, but it has 7 mains of all:
- Phishing Attacking
- Man In the Middle attacking (MITD)
- SQL injection attacking
- Brute Force - attacking password
-Domain Name Sever (DNS) attacking
- DOS and DDOS attacking
What is Phishing attacking?

Phising attacking
Phishing is a type of hacking, this hacking style will steal the profile, information, data, ... of someone, then use this for bad activity like: Impersonation, deceive someone, revision the thing that stealing,...
The Phising attacking always has 4 steps
First step: Find someone then prepare to attacking the victim. Then, the hacker will choosse a business to Impersonation. (Make a Plan)
Second step: Hacker Spreads the email and take some information like using a fake email or fake website.
Third step: The hacker send email to the victim.
Fourth step: The hacker collect some information of victim under some website or pop-up that victim click and fill in the information
Fifth step: The hacker use informations that collect to do bad activity.
What is Man In the Middle attacking (MITD)?
MITD is a hacking style that hacker like a eavesdroper. It works like: a hacker connect a computer then exchange data to this computer, the victim thought that connect direct to a computer or sever. BUT, the truth is the victim is connecting to a host is hacker then the hacker send the data to the sever. So, in this hacking style, the hacker can collect the data or change the data to the sever.
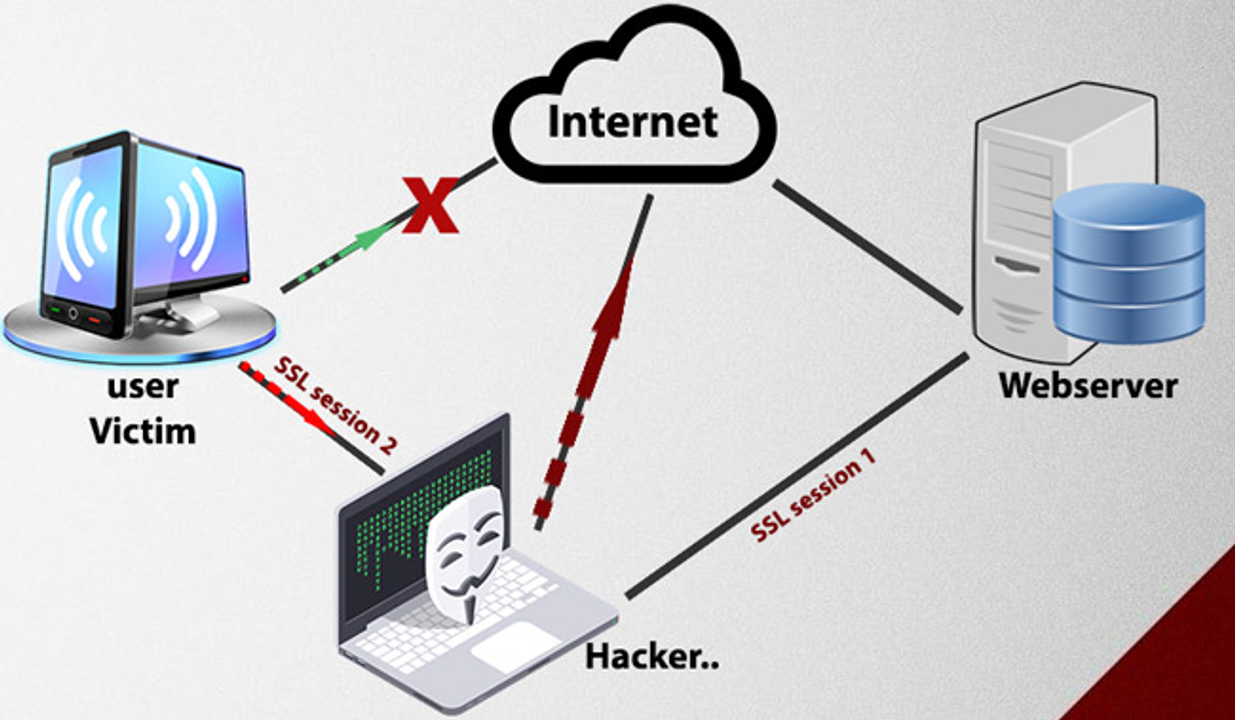
MITD attacking
What is SQL injection attacking?
SQL injection attacking is a style of web hacking that hacker inject some SQL code to input before into web browsers to handle. You can log in without usernames, passwords, or collect datas,...
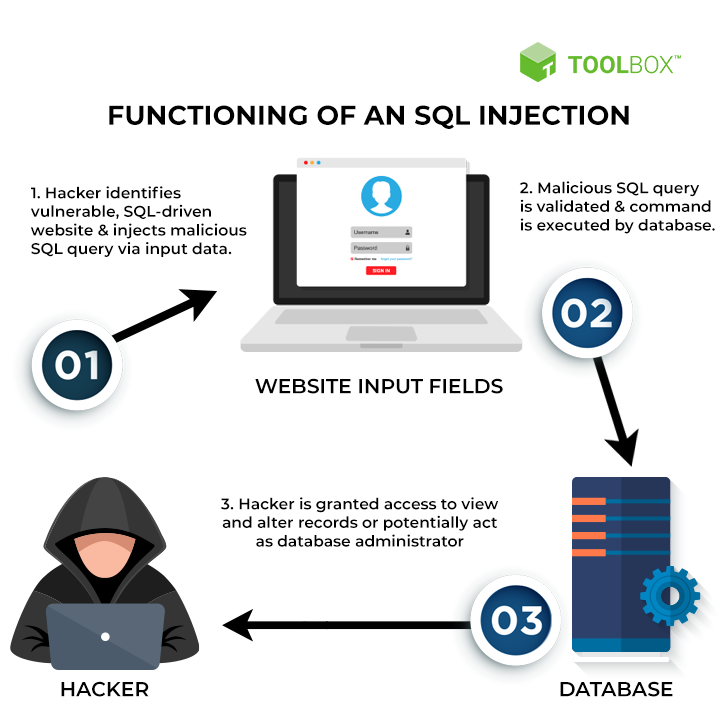
Three steps of SQL injection
What Brute Force hacking?
Brute Force hacking is a style of password hacking. Brute Force that find the password of victim. To find them, Brute Force using Maths to find the passwords. It works like: use some example password of the hacker or the database of the sever, next it check a or some password. If wrong, it will changes a or some characters of passwords until the password is correct. This hacking won't using any hard skill, the basic is it use Math to find passwords by checking skill in Math. So, the password is easier that hacker can find it easy. But, the password is more harder, the hacker can't find it easier or spend very long time to find it.

How it works?

I want to tell about "DNS attacking" and "DOS, DDOS attacking" at next post because it is very long.
What is hacker?
A people has did the hacking is a hacker. Hacker is a person has an advanced skill at programming like an engineer programming, cyber, or pro programmer. It has many types of hacker like:
-Script kiddie: A people doesn't have any programming skill but want to hack. So they use some example code of other people have skill or using tool by guide on social media. This type of hacker like a "trẻ trâu", they don't know how to code and how it works but want to code to showing off or conceited.
-White hacker: A people have skill and morality. White hacker always find bugs and errors of system that can catch problems for the system, they will fix it or call to the host to fix them. The white hacker also have certificate, advanced skill at programming, or more....
-Black Hacker: A people have advanced skill but very evil. They access without accept of host to a severy, system or website. They collect victim's information and use this for bad.
-Grey Hacker: People have skill at programming. In normal, they are good like white hacker. But sometime, they like black hacker. The Grey hacker is also a newbie of programming. They want to learn something about programming and hacking. The Grey hacker is also the middle at Black hacker and White hacker.
So, How to protect the system, account,... before attacker?
To proter your system, account,... you must have:
- A hard password, the hard password also very long, also has special characters, with words and numbers (The character of password must be > 8 characters)
- Turn on firewall, system protection, system security, install antivirus,....

English Zone
/english-zone
Bài viết nổi bật khác
- Hot nhất
- Mới nhất